babyvm wp
大佬给的练习题,应该是根据广外2019比赛babyvm改的,自己也是第一次接触vm的ctf题,很简单,记录下。
题目下载地址:
链接:https://pan.baidu.com/s/1fWfikdoviwZ2PnkCi2p2zA
提取码:4gbf
载入IDA,F5查看主函数
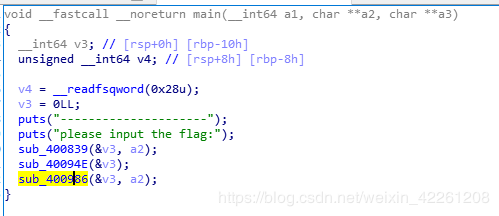
有三个函数,进一步查看
sub_400839
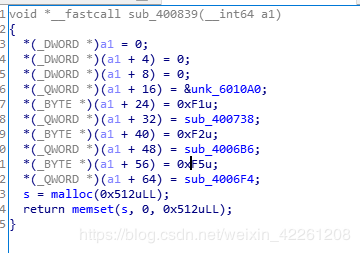
此函数为VM的初始化过程,6010A0为vm操作码的内容,0xf1代表sub_400738函数,0xf2代表sub_4006B6函数,0xf5代表sub_4006F4函数
unk_6010A0内容(截取部分)
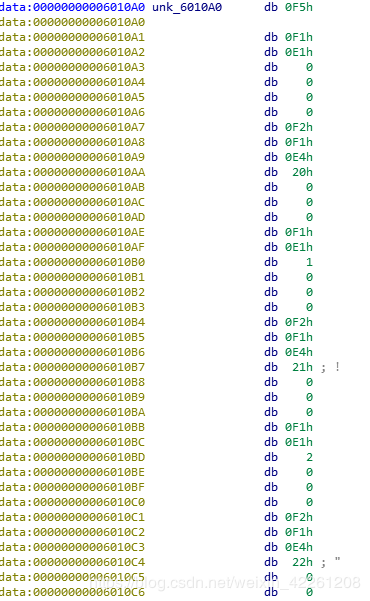
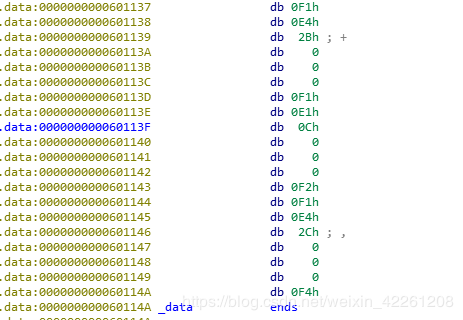
sub_400738(0xf1)
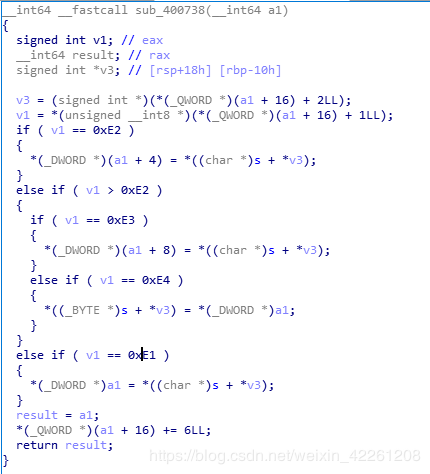
分析可知0xF1代表的是MOV指令,操作数0xE1,0xE2,0xE3,0xE4各自代表不同的寄存器赋值。其中0xE4表示将寄存器赋值给栈s中。
sub_4006B6 (0xf2)
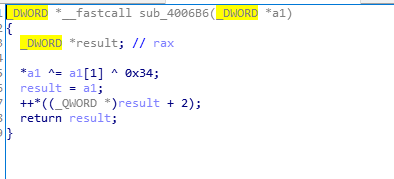
0xf2代表异或, xor,与0x34异或。
其中a1^ =a1[1]^0x34,中a[1]的值为0
sub_4006F4 (0xf5)
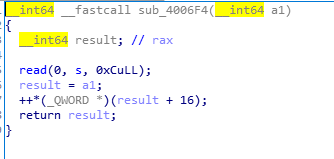
0xf5为read()函数
sub_40094e
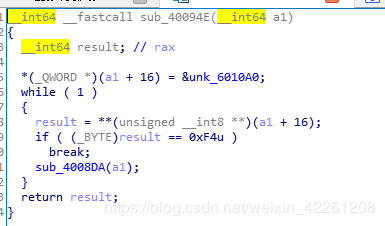
该函数是对6010A0操作码内容的执行,一直到0xf4结束
sub_400986
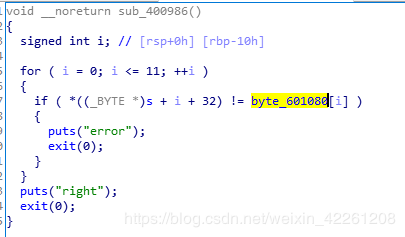
非常明显,这是一个check函数,异或加密后输入内容,与byte_601080的内容进行对比。这里注意的是,我们输入的内容在经过异或加密后存储地址变更为s[0x20]~s[0x2c]。
0x1 虚拟化指令分析unk_6010A0内容
0xf5,
0xf1,0xe1,0x0,0x0,0x0,0x0,
0xf2,
0xf1,0xe4,0x20,0x0,0x0,0x0,
0xf1,0xe1,0x1,0x0,0x0,0x0,
0xf2,
0xf1,0xe4,0x21,0x0,0x0,0x0,
0xf1,0xe1,0x2,0x0,0x0,0x0,
0xf2,
0xf1,0xe4,0x22,0x0,0x0,0x0,
0xf1,0xe1,0x3,0x0,0x0,0x0,
0xf2,
0xf1,0xe4,0x23,0x0,0x0,0x0,
0xf1,0xe1,0x4,0x0,0x0,0x0,
0xf2,
0xf1,0xe4,0x24,0x0,0x0,0x0,
0xf1,0xe1,0x5,0x0,0x0,0x0,
0xf2,
0xf1,0xe4,0x25,0x0,0x0,0x0,
0xf1,0xe1,0x6,0x0,0x0,0x0,
0xf2,
0xf1,0xe4,0x26,0x0,0x0,0x0,
0xf1,0xe1,0x7,0x0,0x0,0x0,
0xf2,
0xf1,0xe4,0x27,0x0,0x0,0x0,
0xf1,0xe1,0x8,0x0,0x0,0x0,
0xf2,
0xf1,0xe4,0x28,0x0,0x0,0x0,
0xf1,0xe1,0x9,0x0,0x0,0x0,
0xf2,
0xf1,0xe4,0x29,0x0,0x0,0x0,
0xf1,0xe1,0xa,0x0,0x0,0x0,
0xf2,
0xf1,0xe4,0x2a,0x0,0x0,0x0,
0xf1,0xe1,0xb,0x0,0x0,0x0,
0xf2,
0xf1,0xe4,0x2b,0x0,0x0,0x0,
0xf1,0xe1,0xc,0x0,0x0,0x0,
0xf2,
0xf1,0xe4,0x2c,0x0,0x0,0x0,
0xf4
分析结果:
read
r1 = s[0]
r1 ^= 0x34
s[0x20] = r1
r1 = s[1]
r1 ^= 0x34
s[0x21] = r1
r1 = s[2]
r1 ^= 0x34
s[0x22] = r1
r1 = s[3]
r1 ^= 0x34
s[0x23] = r1
r1 = s[4]
r1 ^= 0x34
s[0x24] = r1
r1 = s[5]
r1 ^= 0x34
s[0x25] = r1
r1 = s[6]
r1 ^= 0x34
s[0x26] = r1
r1 = s[7]
r1 ^= 0x34
s[0x27] = r1
r1 = s[8]
r1 ^= 0x34
s[0x28] = r1
r1 = s[9]
r1 ^= 0x34
s[0x29] = r1
r1 = s[10]
r1 ^= 0x34
s[0x2a] = r1
r1 = s[11]
r1 ^= 0x34
s[0x2b] = r1
r1 = s[12]
r1 ^= 0x34
s[0x2c] = r1
ret
0x2 解密s=[’\x75’,’\x6b’,’\x51’,’\x00’,’\x47’,’\x6d’,’\x6b’,’\x42’,’\x59’,’\x15’,’\x15’,’\x15’,]
flag=’’
l=len(s)
s=list(map(ord,s))
for i in range(l):
num=s[i]^0x34
flag+=chr(num)
print(flag)
flag:A_e4sY_vm!!!
作者:winterze