APP 安全测试(OWASP Mobile Top 10)--后篇之二
接续:APP 安全测试(OWASP Mobile Top 10)--后篇之一
M7- 客户端代码质量测试点:
将不受信任的输入传递给移动代码中的方法调用的实体 Activity组件本地拒绝服务 Activity劫持 Activity组件绕过 Broadcast Receiver组件本地拒绝服务 Broadcast盗窃 恶意Broadcast注入 Content Provider组件本地拒绝服务 Service组件本地拒绝服务 Service劫持 恶意Activity/Service调用 Symbols Remnant 弱Check-sum控制/改变检查 Unix domain sockets的不安全权限 不安全网络sockets的使用 本地数据文件存储安全 调试信息是否关闭 第三方SDK安全性检测 留存的测试组件或信息 代码中不当的异常处理 保留的内网地址信息 数字签名检测测试说明:
1. 黄色部分测试的是apk中的四大组件
2. 蓝色部分反编译后的具体代码分析
3. 其他
测试方法会按照上面的三部分来说明:
1. 黄色部分测试的是apk中的四大组件
1.1 测这块需要安装drozer,因为我的系统是kali,所以直接运行apt-get install drozer就能直接安全
1.2 手机端配置一下drozer angent(具体安装以查看drozer 安装:https://www.cnblogs.com/lsdb/p/9441813.html)
1.3 drozer使用:
adb devices
adb forward tcp:31415 tcp:31415
drozer console connect
dz> run app.package.list -f ****
2. 查找你要测试得apk包
dz> run app.package.list -f aaa
com.aaa.mobile
com.aaa.cloud
3. 查看要测试得包信息和权限信息(前面用的Andriod killer,用drozer的这边的命令也可以查看)
dz> run app.package.info -a com.aaa.mobile
Package: com.aaa.mobile
Application Label: *****
Process Name: com.aaa.mobile
Version: 4.6.2
Data Directory: /data/user/0/com.aaa.mobile
APK Path: /data/app/com.aaa.mobile-lUXFRNxY8xKsNgdzr04RIA==/base.apk
UID: 10193
GID: [3002, 3003, 3001]
Shared Libraries: [/system/framework/org.apache.http.legacy.boot.jar]
Shared User ID: null
Uses Permissions:
- android.permission.CALL_PHONE
- android.permission.SYSTEM_ALERT_WINDOW
- android.permission.ACCESS_WIFI_STATE
- android.permission.BLUETOOTH
- android.permission.INTERNET
- android.permission.BLUETOOTH_ADMIN
- android.permission.ACCESS_NETWORK_STATE
- com.android.launcher.permission.READ_SETTINGS
- android.permission.WAKE_LOCK
- android.permission.CHANGE_WIFI_STATE
- android.permission.WRITE_EXTERNAL_STORAGE
- android.permission.WRITE_SETTINGS
- android.permission.ACCESS_COARSE_LOCATION
- android.permission.ACCESS_FINE_LOCATION
- android.permission.READ_PHONE_STATE
- android.permission.CHANGE_CONFIGURATION
- android.permission.CAMERA
- android.permission.RECORD_VIDEO
- android.permission.USE_FINGERPRINT
- android.permission.READ_LOGS
- android.permission.READ_EXTERNAL_STORAGE
- android.permission.GET_TASKS
- android.permission.SENSOR_INFO
- android.permission.SENSOR_ENABLE
- android.permission.KILL_BACKGROUND_PROCESSES
- android.permission.READ_CALENDAR
- android.permission.WRITE_CALENDAR
- android.permission.RECEIVE_BOOT_COMPLETED
- android.permission.ACCESS_LOCATION_EXTRA_COMMANDS
- android.permission.CHANGE_NETWORK_STATE
- android.permission.FLASHLIGHT
- android.permission.VIBRATE
- com.aaa.mobile.permission.C2D_MESSAGE
- com.aaa.mobile.permission.JPUSH_MESSAGE
- android.permission.RECEIVE_USER_PRESENT
- android.permission.MOUNT_UNMOUNT_FILESYSTEMS
- android.permission.RECORD_AUDIO
- android.permission.MODIFY_AUDIO_SETTINGS
- android.permission.BROADCAST_STICKY
- com.aaa.mobile.permission.RECEIVE_MSG
- com.aaa.mobile.permission.MIPUSH_RECEIVE
- com.meizu.flyme.push.permission.RECEIVE
- com.aaa.mobile.push.permission.MESSAGE
- com.meizu.c2dm.permission.RECEIVE
- android.permission.RESTART_PACKAGES
- com.google.android.c2dm.permission.RECEIVE
- com.sec.android.provider.badge.permission.READ
- com.sec.android.provider.badge.permission.WRITE
- com.htc.launcher.permission.READ_SETTINGS
- com.htc.launcher.permission.UPDATE_SHORTCUT
- com.sonyericsson.home.permission.BROADCAST_BADGE
- com.sonymobile.home.permission.PROVIDER_INSERT_BADGE
- com.anddoes.launcher.permission.UPDATE_COUNT
- com.majeur.launcher.permission.UPDATE_BADGE
- com.huawei.android.launcher.permission.CHANGE_BADGE
- com.huawei.android.launcher.permission.READ_SETTINGS
- com.huawei.android.launcher.permission.WRITE_SETTINGS
- android.permission.READ_APP_BADGE
- com.oppo.launcher.permission.READ_SETTINGS
- com.oppo.launcher.permission.WRITE_SETTINGS
- me.everything.badger.permission.BADGE_COUNT_READ
- me.everything.badger.permission.BADGE_COUNT_WRITE
Defines Permissions:
- com.aaa.mobile.permission.C2D_MESSAGE
- com.aaa.mobile.permission.JPUSH_MESSAGE
- com.aaa.mobile.permission.RECEIVE_MSG
- com.aaa.mobile.permission.MIPUSH_RECEIVE
- com.aaa.mobile.push.permission.MESSAGE
- com.aaa.mobile.permission.C2D_MESSAGE
4. 查看攻击面
dz> run app.package.attacksurface com.aaa.mobile
Attack Surface:
4 activities exported
13 broadcast receivers exported
2 content providers exported
4 services exported
5. 上面可以看到4大组件都存在攻击面,下面需要各个来查看处理
6. Activity组件测试
dz> run app.activity.info -a com.aaa.mobile
Package: com.aaa.mobile
com.aaa.mobile.DefaultActivity
Permission: null
Target Activity: com.aaa.mobile.Activity
com.aaa.mobile.wxapi.WEnActivity
Permission: null
com.ug.qq.tencent.AuthActivity
Permission: null
cn.jpush.android.service.JNoActivity
Permission: null
7. Activity 劫持,使用攻击hijackactivity.apk,需要将该工具装到要测试的手机上面:

可以将要测试的app添加到里面,如果app可以被劫持的话,打开app就会一直处于顶端。
8. Activity 绕过:
dz> run app.activity.start --component com.aaa.mobile.wxapi.WXEntryActivity com.umeng.qq.tencent.AuthActivity cn.jpush.android.service.JNotifyActivity
unrecognized arguments: cn.jpush.android.service.JNotifyActivity
dz> run app.activity.start --component com.aaa.mobile.wxapi.WXEntryActivity com.umeng.qq.tencent.AuthActivity
Unable to find explicit activity class {com.aaa.mobile.wxapi.WXEntryActivity/com.umeng.qq.tencent.AuthActivity}; have you declared this activity in your AndroidManifest.xml?
dz> run app.activity.start --component com.aaa.mobile.wxapi.WXEntryActivity cn.jpush.android.service.JNotifyActivity
Unable to find explicit activity class {com.aaa.mobile.wxapi.WXEntryActivity/cn.jpush.android.service.JNotifyActivity}; have you declared this activity in your AndroidManifest.xml?
dz> run app.activity.start --component com.umeng.qq.tencent.AuthActivity com.aaa.mobile.wxapi.WXEntryActivity
Unable to find explicit activity class {com.umeng.qq.tencent.AuthActivity/com.aaa.mobile.wxapi.WXEntryActivity}; have you declared this activity in your AndroidManifest.xml?
dz> run app.activity.start --component com.umeng.qq.tencent.AuthActivity cn.jpush.android.service.JNotifyActivity
Unable to find explicit activity class {com.umeng.qq.tencent.AuthActivity/cn.jpush.android.service.JNotifyActivity}; have you declared this activity in your AndroidManifest.xml?
dz> run app.activity.start --component cn.jpush.android.service.JNotifyActivity om.aaa.mobile.wxapi.WXEntryActivity
Unable to find explicit activity class {cn.jpush.android.service.JNotifyActivity/om.aaa.mobile.wxapi.WXEntryActivity}; have you declared this activity in your AndroidManifest.xml?
dz> run app.activity.start --component cn.jpush.android.service.JNotifyActivity com.aaa.mobile.wxapi.WXEntryActivity
Unable to find explicit activity class {cn.jpush.android.service.JNotifyActivity/com.aaa.mobile.wxapi.WXEntryActivity}; have you declared this activity in your AndroidManifest.xml?
dz> run app.package.attacksurface com.aaa.mobile
上面可以看到没有执行主页面defaultActivity,直接执行的是后面几个没有授权的Activity,如果该处存在绕过漏洞会直接调到相应的界面。
9. Broadcat 组件测试:
dz> run app.broadcast.info -a com.aaa.mobile
Package: com.aaa.mobile
com.aaa.mobile.broadcast.MyBlueToothReceiver
Permission: null
com.google.android.gms.gcm.GcmReceiver
Permission: com.google.android.c2dm.permission.SEND
cn.jpush.android.service.PushReceiver
Permission: null
com.aaa.mobile.jpush.aaaReceiver
Permission: null
com.xiaomi.push.service.receivers.NetworkStatusReceiver
Permission: null
cn.jpush.android.service.PluginXiaomiPlatformsReceiver
Permission: null
cn.jpush.android.service.PluginHuaweiPlatformsReceiver
Permission: null
com.aaa.mobile.nim.HuaWeiReceiver
Permission: null
cn.jpush.android.service.PluginMeizuPlatformsReceiver
Permission: null
com.aaa.mobile.nim.MeizuReceiver
Permission: null
org.altbeacon.beacon.startup.StartupBroadcastReceiver
Permission: null
com.learnium.RNDeviceInfo.RNDeviceReceiver
Permission: null
com.google.firebase.iid.FirebaseInstanceIdReceiver
Permission: com.google.android.c2dm.permission.SEND
10. Broadcast“盗窃”:
上面查看aaa相关的broadcast组件:
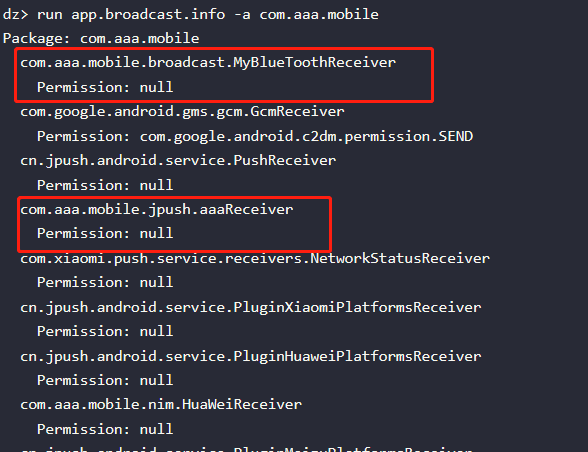
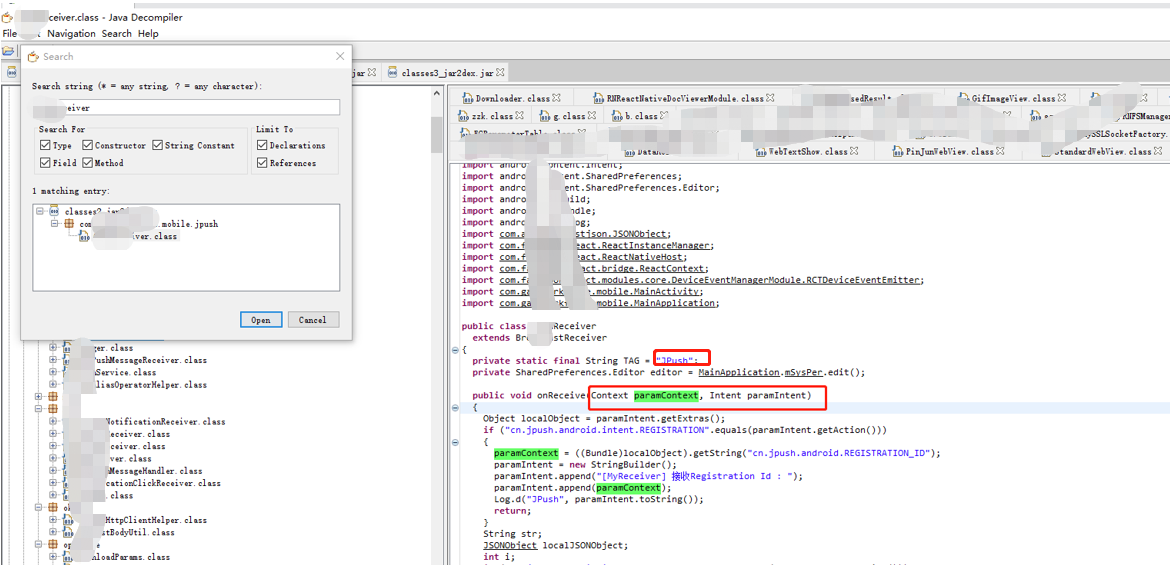
以后一个broadcast为例, com.aaa.mobile.jpush.aaaReceiver.查看反编译的源码搜索“aaaReceiver”,发现有两个参数如下:
执行“盗窃”行为,看能不能执行:
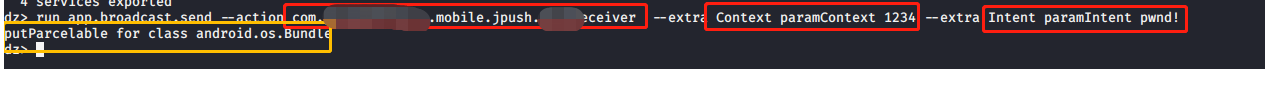
从上面执行结果中可以看到执行命令没有报错,而且走到了执行参数那边。
11. Content provier查询,这边因为我的drozer finduris命令执行一直有问题,所以没有进行后续,但content这块涉及到的内容比较多,下次有会单独对这块写一篇博客。
dz> run scanner.provider.finduris -a com.aaa.mobile
12. Service
1. 查看service 信息
dz> run app.service.info -a com.aaa.mobile
2. service 启动:

这边启动成功后,要adb shell查看这些服务有没有正常启动成功: ps -ef | grep service名称
上面基本上是这次四大组件的测试方法,除了content这边我会另外单独写一篇博客来说明一下。
未完待续:APP 安全测试(OWASP Mobile Top 10)--后篇之三
作者:fiona_xlh